Key research themes
1. How can simulation and virtual tools enhance the teaching and practical understanding of network design and security?
This research theme addresses the challenge of effectively teaching complex networking concepts and security protocols using simulation environments and virtual tools. It highlights how integrating these tools in academic curricula bridges the gap between theoretical knowledge and practical skills, improves student engagement, and prepares students for real-world network management and security challenges. The focus is on evaluating different simulation platforms and virtual labs tailored for educational purposes.
2. What are effective methods to optimize content placement and caching strategies in Content-Centric Networking to enhance overall network performance?
Focusing on the optimization of in-network caching within Content-Centric Networking (CCN), this theme investigates strategies to minimize content redundancy, maximize cache hit ratios, and improve latency and link load. The research explores mathematical and algorithmic content placement policies that consider request rates, node distances, and cache availability, aiming to achieve balanced, efficient data dissemination suitable for future networks such as IoT and vehicular networks.
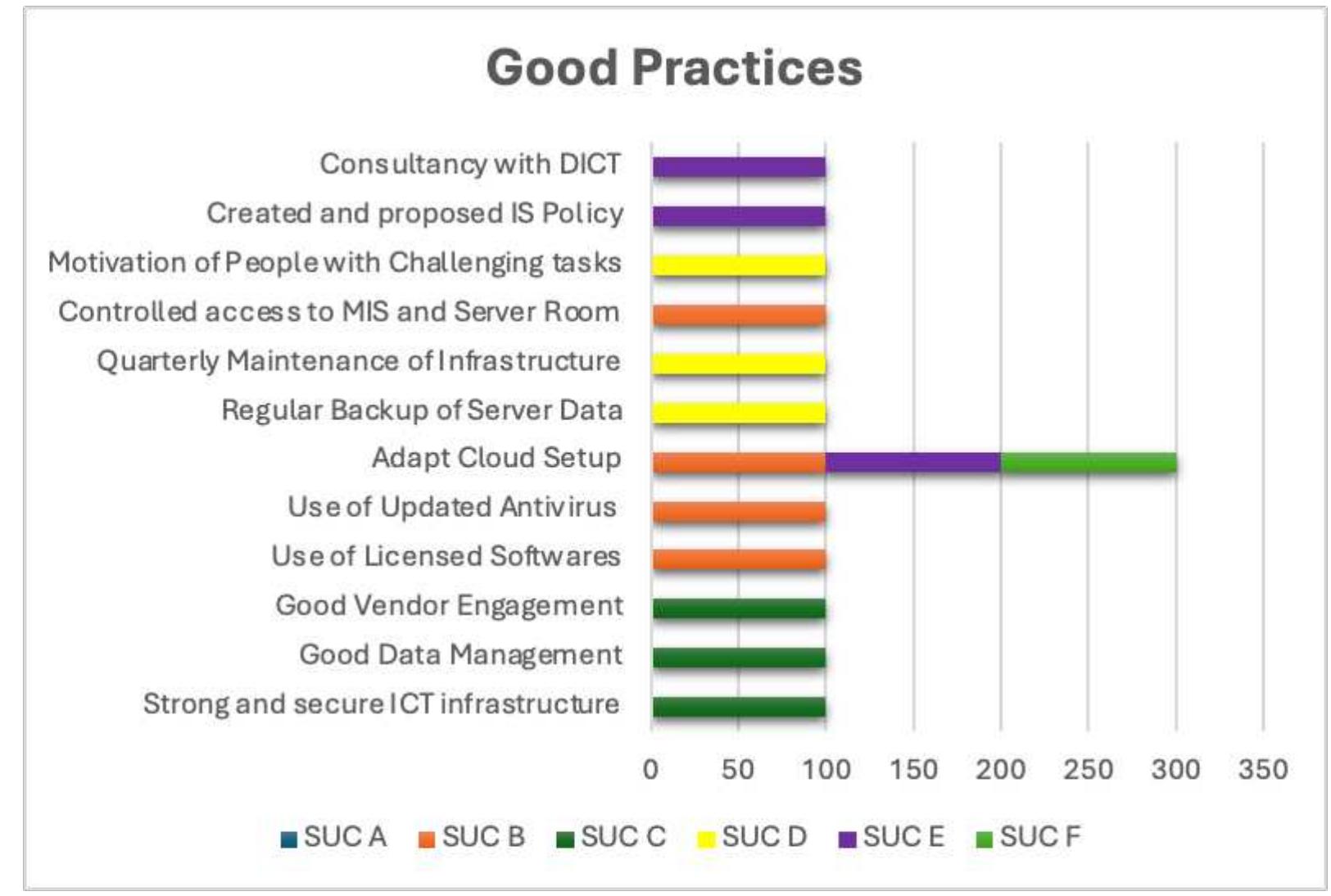
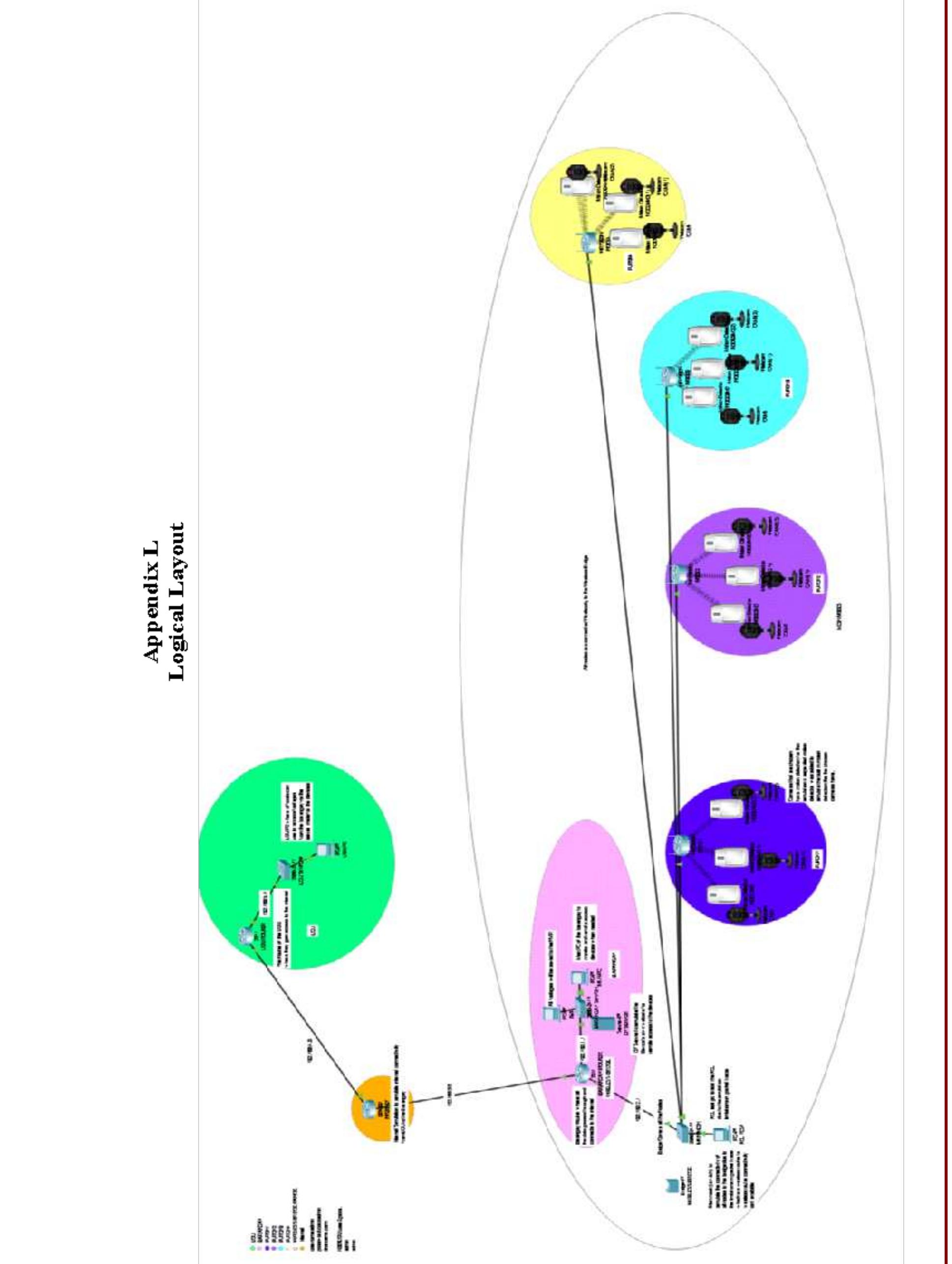
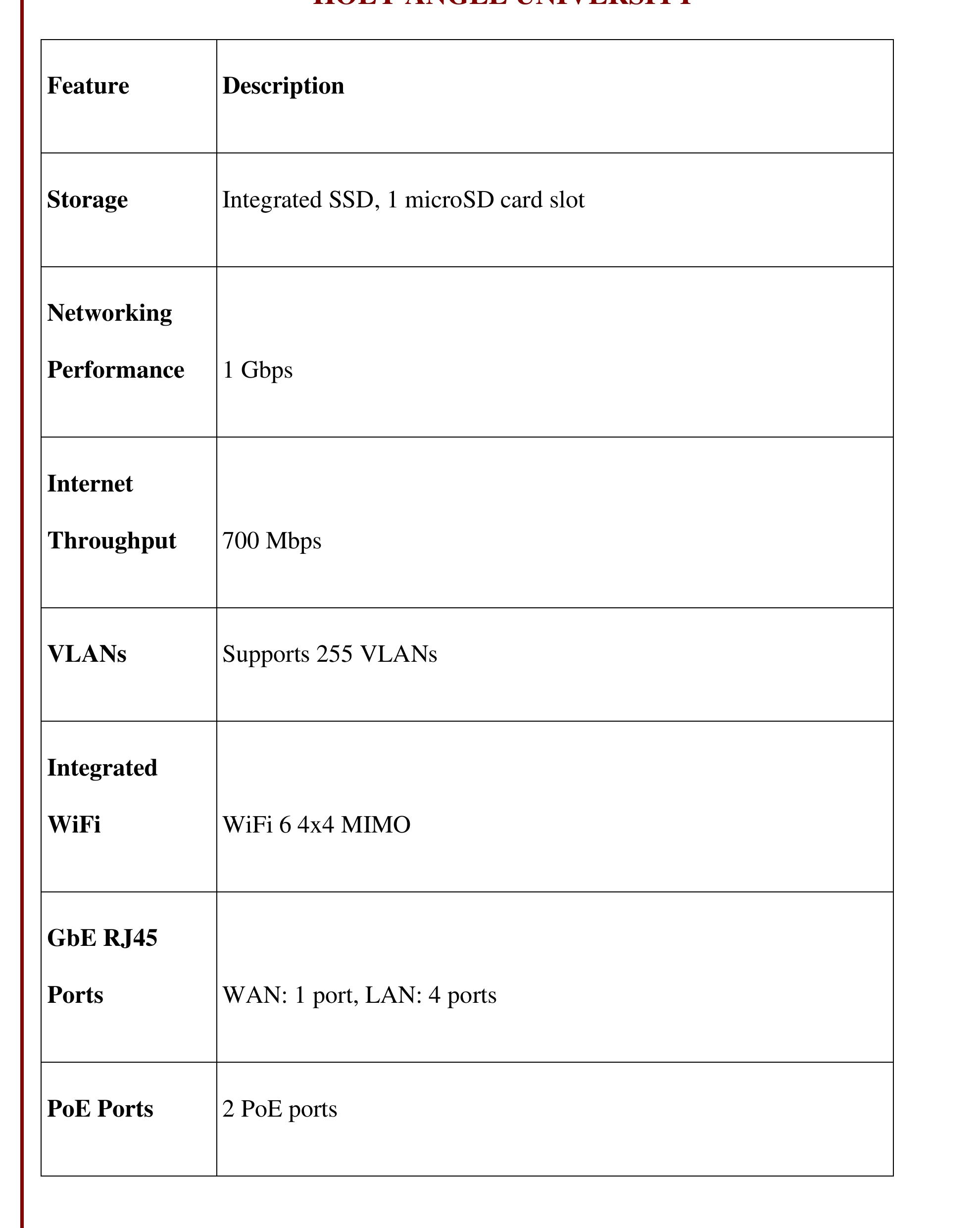
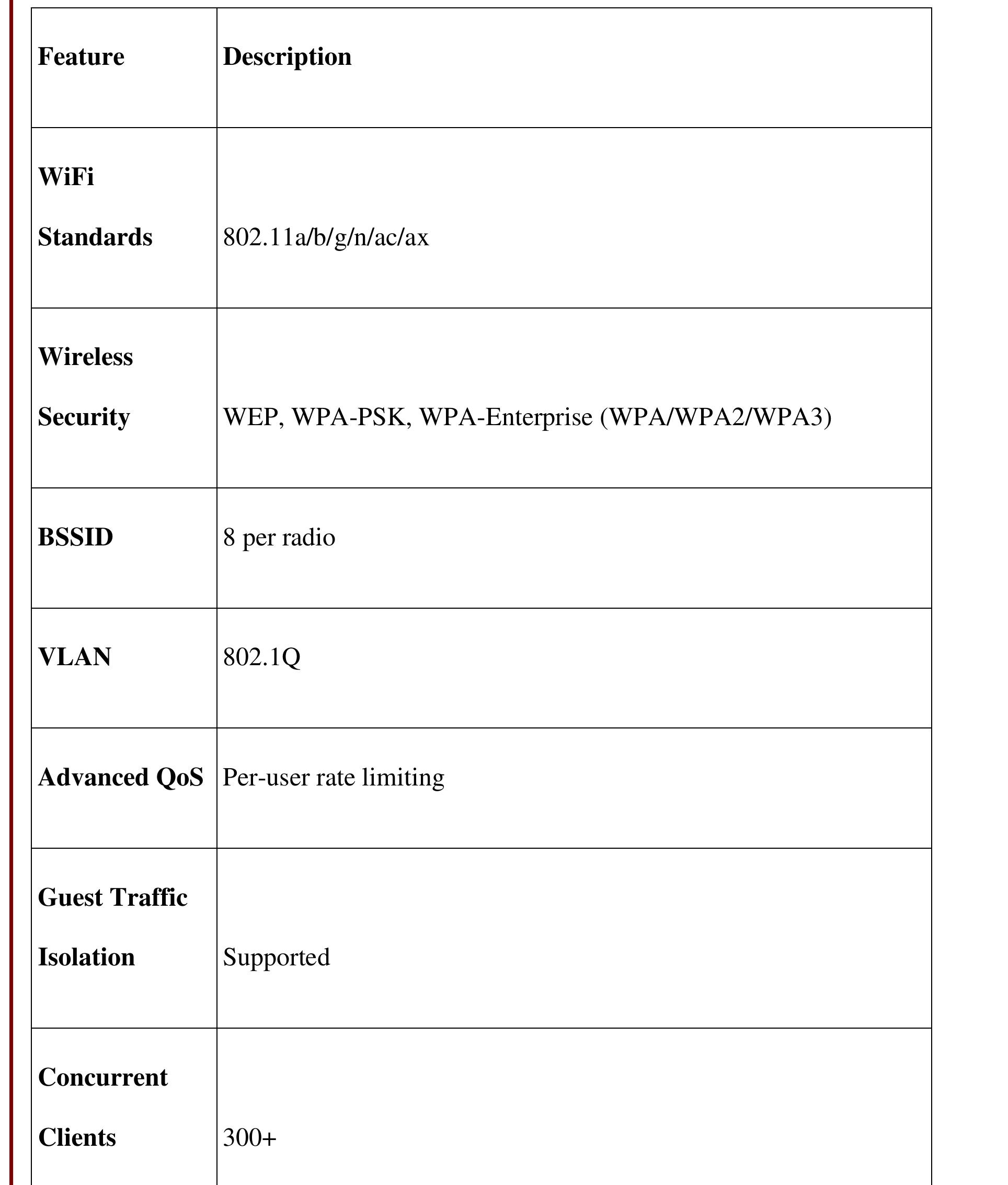
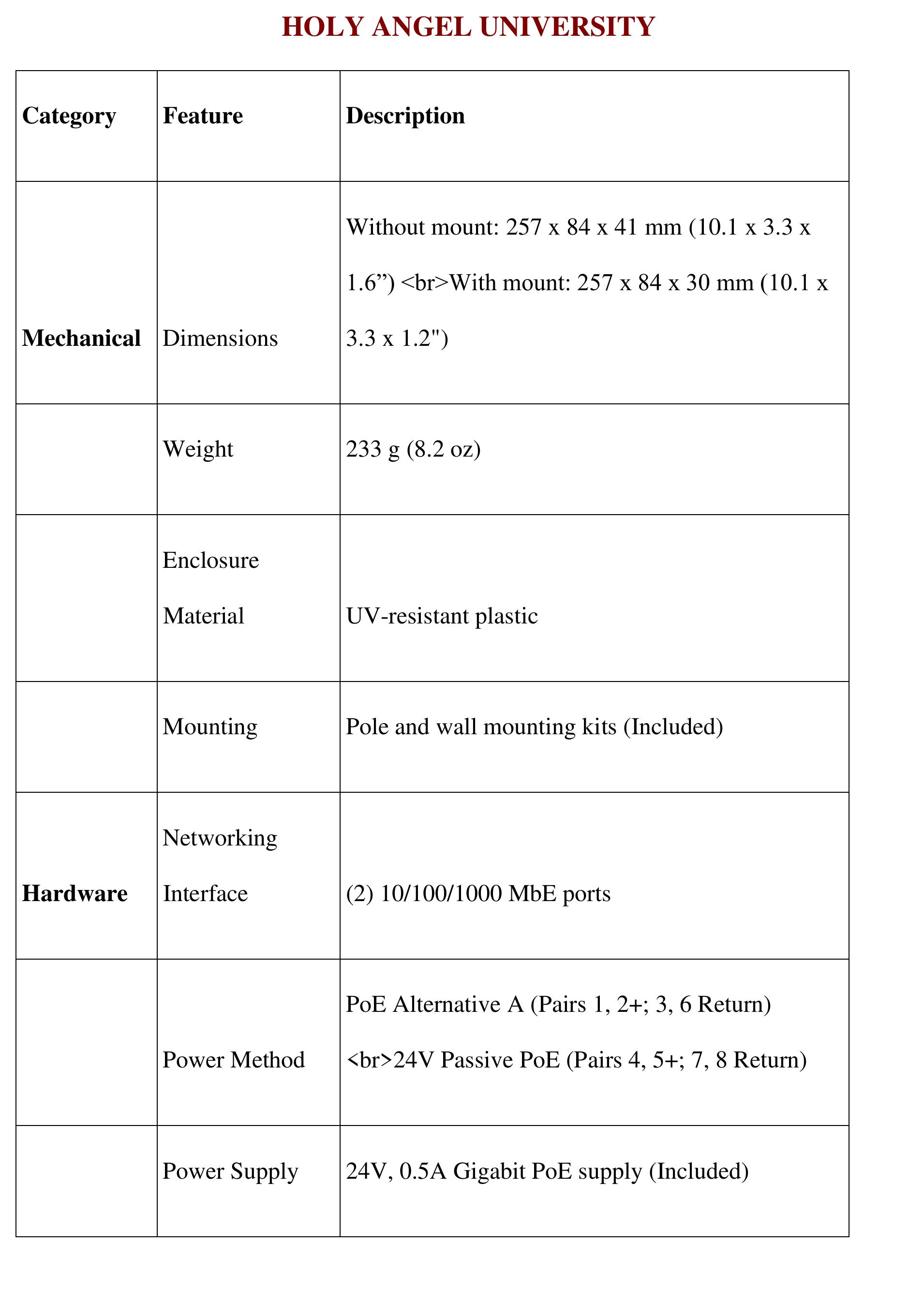
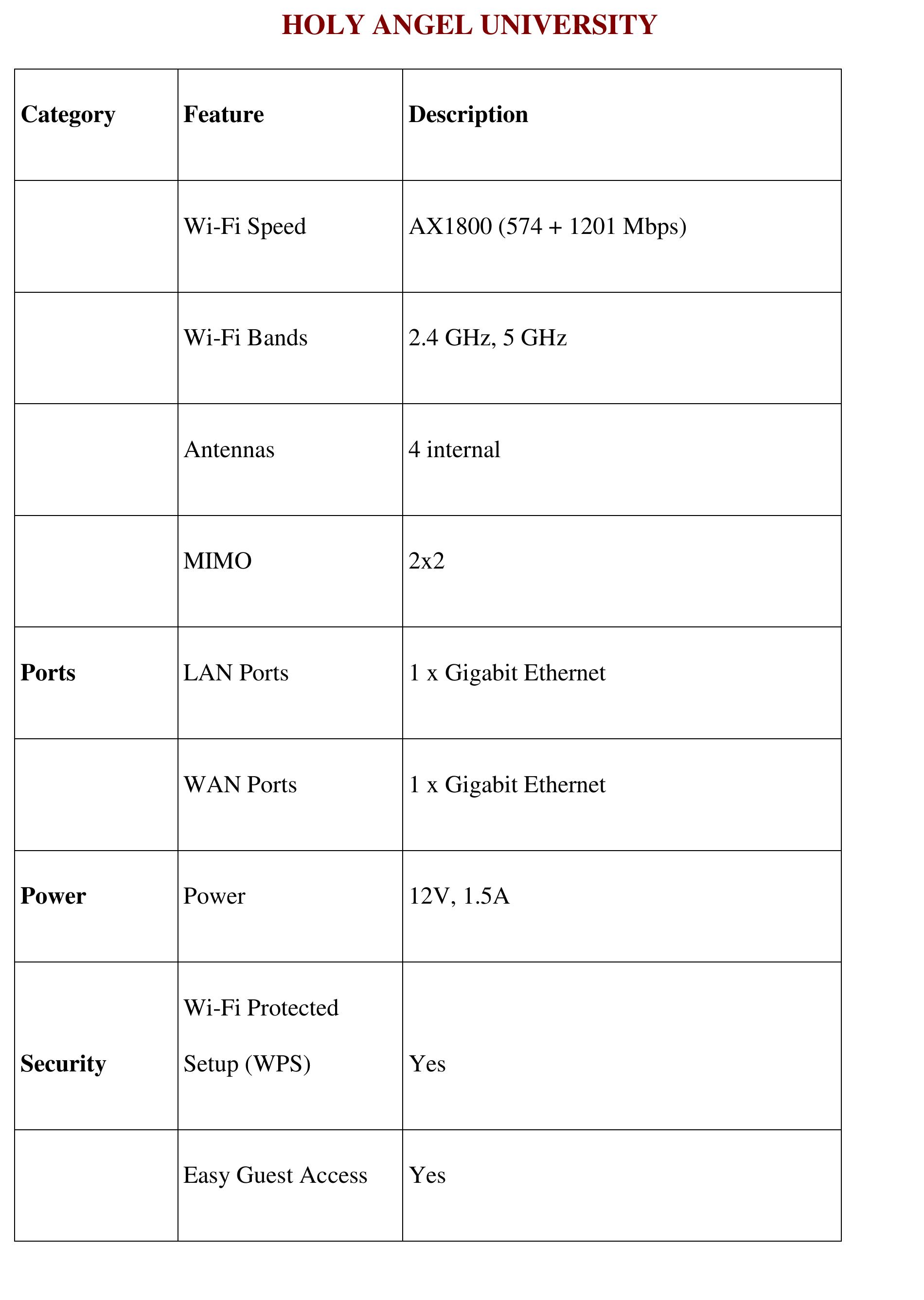
3. How can security in wireless and computer networks be strengthened through advanced protocols, awareness, and infrastructure design?
This research area explores methodologies and practical implementations to enhance the security posture of wireless and computer networks. It covers secure communication protocols like WPA3, intrusion detection/prevention systems, user behavior analysis, regulatory compliance, simulation of secure network topologies, and awareness programs. Emphasis is placed on addressing both technological and human-factor vulnerabilities to safeguard network data, optimize privacy, and resist social engineering and cyber-attacks.