We propose a novel bio-inspired solution for biomedical article classification. Our method draws from an existing model of T-cell cross-regulation in the vertebrate immune system (IS), which is a complex adaptive system of millions of... more
This paper presents the use of corpus linguistics techniques on supposedly "clean" corpora and identifies potential pitfalls. Our work relates to the task of filtering sensitive content, in which data security is strategically important... more
In this paper we describe an approach to information assurance in which we can prevent breach of confidentiality. Specifically, we examine aspects of the propagation of confidential information via email. Email provides one simple... more
E-commerce sites, forums, and blogs have become popular platforms for people to share their views. Reviews have emerged as a crucial source of information for potential customers, influencing their purchasing decisions. Similarly for... more
In today’s world, fake review identification and prediction is an importantarea of sentiment analysis of the E-commerce industry. The automatic fake review categorizersidentify and categorize a variety of duplicate, spam, fake and... more
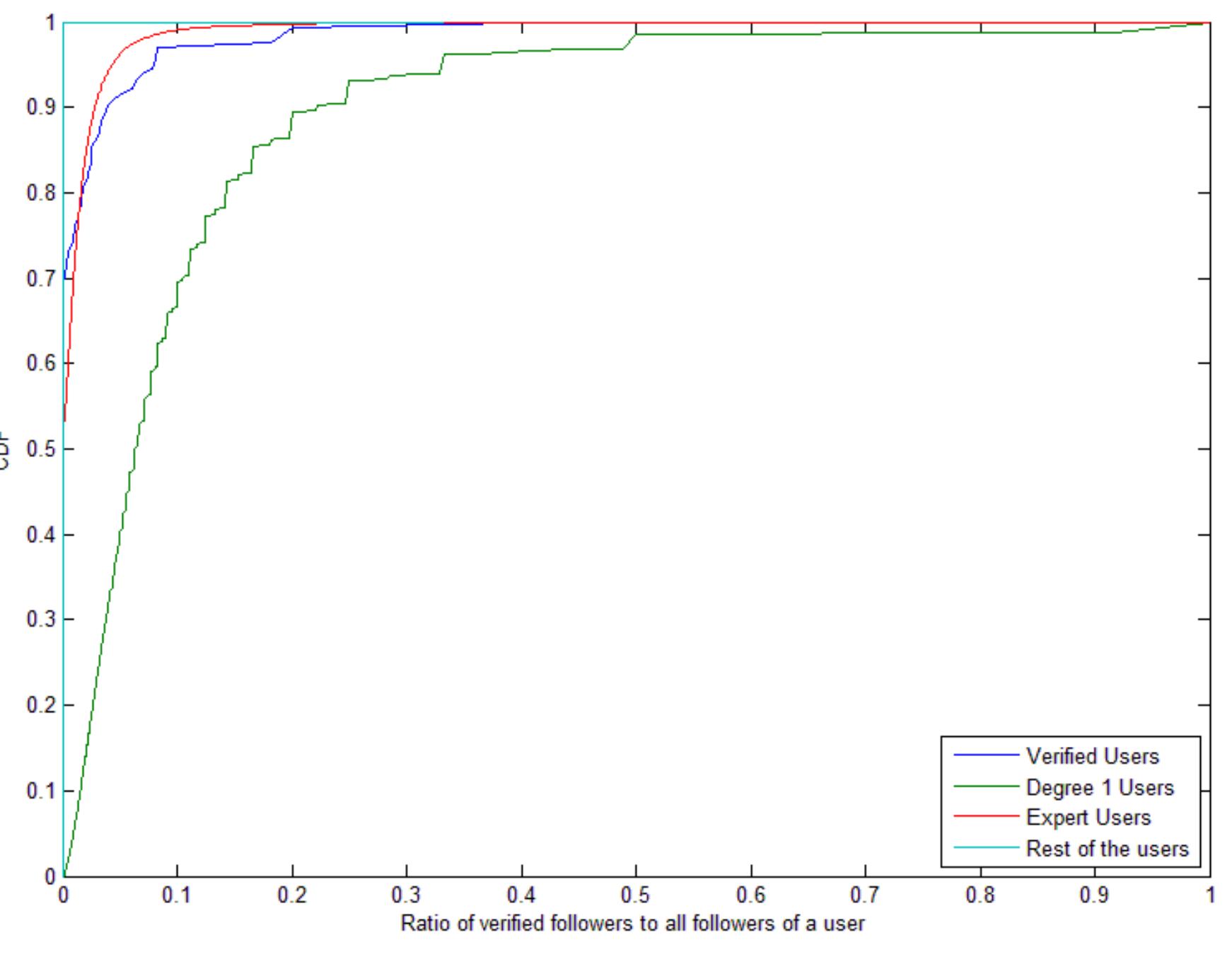
Online Social Networks (OSNs), such as Twitter, offer attractive means of social interactions and communications, but also raise privacy and security issues. The OSNs provide valuable information to marketing and competitiveness based on... more
To the modern Search Engines (SEs), one of the biggest threats to be considered is spamdexing. Nowadays spammers are using a wide range of techniques for content generation, they are using content spam to fill the Search Engine Result... more
The paper reviews various approaches for detecting fake reviews using different machine learning techniques, each with distinct strengths and limitations. It examines existing literature on supervised learning methods, unsupervised... more
The exponential growth of mobile communication has intensified the threat of SMS spam, compromising user security and trust in messaging platforms. This study addresses this challenge by designing and deploying a robust spam detection... more
In this paper, the clustering Algorithm known as Support Vector Classifier (SVC) is used. SVC offers classifiers such as logistic regression and decision trees that provide very high accuracy compared to others. The model first... more
Users of all ages face risks on social media and messaging platforms. When encountering suspicious messages, legitimate concerns arise about a sender's malicious intent. This study examines recent advances in Natural Language Processing... more
Online credibility is a quality pursued by users, business and brands on Internet. Having a verified page on Facebook means improvement of the social web presence, reliability and reinforcement of security against impersonations of... more
The article explores fundamental techniques for converting text into numerical data for machine learning algorithms. It meticulously examines various methods, including word vector representation via neural networks like Word2Vec, and... more
Communicating by email has become crucial for all companies today. However, a significant amount of undesirable messages pass through mail servers. Such unwanted and unsolicited communications are responsible for a significant loss of... more
this research project acts as a foundational guide for students and early-career professionals interested in AI. It combines academic theory, technical practice, and ethical reflection to provide a holistic understanding of AI and machine... more
Abstract: There are economic and socio-cultural differences that characterise the north and south of Italy. A stereotype is that university students from rural southern Italy are more disadvantaged and isolated than those from the urban... more
In the modern era, mobile phones have become ubiquitous, and Short Message Service (SMS) has grown to become a multi-million-dollar service due to the widespread adoption of mobile devices and the millions of people who use SMS daily.... more
The rapid proliferation of mobile communication has kept Short Message Service (SMS) a popular channel for personal and business communications. As the usage rose, the malicious exploitation followed, leading to the increased flow of... more
With the growth of networking the usage of mails are also enhanced. Due to rapid growth of internet, dependency of communication is mostly based on electronics mails for both commercial and business purposes. According to today's... more
With the growth of networking the usage of mails are also enhanced. Due to rapid growth of internet, dependency of communication is mostly based on electronics mails for both commercial and business purposes. According to today's... more
The widespread use of email as a primary communication medium has led to an increase in spam messages, which pose significant threats to privacy, productivity, and cybersecurity. Spam emails, often disguised as legitimate messages, can... more
Phishing remains one of the most prevalent and evolving cybersecurity threats, exploiting humanvulnerabilities through deceptive digital communication. This study proposes a dynamic, Windows-specific phishing detection model leveraging... more
The number of email users is increasing every day worldwide. If you have to communicate officially with someone, whether in a business matter or with someone else, your electronic mail is the best option. When identifying the emails,... more
This study suggests a machine learning-based detection system built with Python and Django to tackle the growing problem of fraudulent profiles on social networking sites. Malicious actors are progressively setting up phony identities for... more
Industrial insider risk assessment using electroencephalogram (EEG) signals has consistently attracted a lot of research attention. However, EEG signal-based risk assessment systems, which could evaluate the emotional states of humans,... more
The spread of misinformation on the internet and social media has become a growing problem, impacting public opinion and decisionmaking. In this study, we explore how machine learning can be used to detect and classify fake news more... more
The advanced architecture of Large Language Models (LLMs) has revolutionised natural language processing, enabling the creation of text that convincingly mimics legitimate human communication, including phishing emails. As AI-generated... more
Nuestro objetivo con este artículo es relacionar las emociones y los estereotipos de género por medio del análisis de las narrativas que contienen los spams. Presentaremos cuatro diferentes tipos de spam de 450 correos electrónicos, que... more
In this article, we aim at relating emotions and gender stereotypes through the analysis of the narratives contained in spam e-mails. We will present four different types of spam e-mails from a corpus consisting of 450 emails, their... more
Phishing, a social Engineering attacks are becoming more common because of the quick digitization of healthcare services. Phishing is often used to steal user data, including login credentials and credit card numbers. It occurs when an... more
Estimating the number of triangles in a graph is one of the most fundamental problems in sublinear algorithms. In this work, we provide the first approximate triangle counting algorithm using only polylogarithmic queries. Our query oracle... more
Phishing, a prevalent social engineering attack, is frequently employed by cybercriminals to steal sensitive user data, including login credentials, credit card information, and confidential government or corporate details. Despite... more
With the continuous rise in the number of mobile device users, SMS (Short Message Service) remains a prevalent communication tool accessible on both smartphones and basic phones. Consequently, SMS traffic has experienced a significant... more
Combatting email spam has remained a very daunting task. Despite the over 99% accuracy in most non-image-based spam email detection, studies on image-based spam hardly attain such a high level of accuracy as new email spamming techniques... more
Information retrieval on the web is significant and furthermore complex activity for web mining. Because of enormously increased the number of websites on the Internet, the execution of PageRank Algorithm should be easy and faster in... more
Abstract. Through their interaction with search engines, users provide implicit feedback that can be used to extract useful knowledge and improve the quality of the search process. This feedback is encoded in the form of a query log that... more
Online Social Networks (OSNs) at present engages the majority of individuals, from the newborn to the elderly. Social networks provide direct connection between people and increased information sharing opportunities to provide a large... more
Grouping resources into set of classes allows easy access to the resources we use in our day-to-day lives. This classification makes the search faster and easier. The process of classifying the resources manually becomes expensive. This... more
Because of its ease of use and speed compared to other communication applications, email is the most commonly used communication application worldwide. However, a major drawback is its inability to detect whether mail content is either... more
Malicious websites are those that are created to harm visitors or exploit their information for illegal purposes. These websites are commonly utilized in attacks, such as phishing, malware distribution, and scams. Clicking on a malicious... more
Email phishing is a manipulative technique aimed at compromising information security and user privacy. To overcome the limitations of traditional detection methods, such as blacklists, this research proposes a phishing detection model... more
The problem of NLP should be divided into several small parts and solved step by step. In this article, where NLP is necessary at every stage of solving the problem, all forms of text processing are considered. The step-by-step text... more
Fake followers are those Twitter accounts specifically created to inflate the number of followers of a target account. Fake followers are dangerous for the social platform and beyond, since they may alter concepts like popularity and... more
Fake followers are those Twitter accounts created to inflate the number of followers of a target account. Fake followers are dangerous to the social platform and beyond, since they may alter concepts like popularity and influence in the... more
Email is an increasingly important and ubiquitous means of communication, both facilitating contact between individuals and enabling rises in the productivity of organizations. However, the relentless rise of automatic unauthorized... more
In this paper, we examine the application of various grouping techniques to help improve the efficiency and reduce the costs involved in an electronic discovery process. Specifically, we create coherent groups of email documents which... more