Analysing the Twitter social graph: Whom can we trust?
2014
Sign up for access to the world's latest research

















Related papers
2019
I declare that this work has not been previously submitted and approved for the award of a degree by this or any other University. To the best of my knowledge and belief, this research thesis contains no material previously published or written by another person except where due reference is made in the thesis itself.
IEEE Access
The importance of information credibility in society cannot be underestimated given that it is at the heart of all decision-making. Generally, more information is better; however, knowing the value of this information is essential for decision-making processes. Information credibility defines a measure of the fitness of information for consumption. It can also be defined in terms of reliability, which denotes the probability that a data source will appear credible to the users. A challenge in this topic is that there is a great deal of literature that has developed different credibility dimensions. Additionally, information science dealing with online social networks has grown in complexity, attracting interest from researchers in information science, psychology, human-computer interaction, communication studies, and management studies, all of whom have studied the topic from different perspectives. This work will attempt to provide an overall review of the credibility assessment literature over the period 2006-2017 as applied to the context of the microblogging platform, Twitter. Known interpretations of credibility will be examined, particularly as they relate to the Twitter environment. In addition, we investigate levels of credibility assessment features. We then discuss recent works, addressing a new taxonomy of credibility analysis and assessment techniques. At last, a cross-referencing of literature is performed while suggesting new topics for future studies of credibility assessment in social media context.
International Journal of Cyber Warfare and Terrorism, 2013
The use of social network sites has exploded with its multitude of functions which include posting pictures, interests, activities and establishing contacts. However, users may be unaware of the lurking dangers of threats originating from Social Networking Sites (SNS) which include malware or fake profiles. This paper investigates the indicators to arouse suspicion that a social networking account is invalid with a specific focus on Facebook as an illustrative example. The results from a survey on users’ opinions on social networks, is presented in the paper. This helps reveal some of the trust indicators that leads users to ascertaining whether a social networking profile is valid or not. Finally, indicators of potentially deceptive agents and profiles are given as a guideline to help users decide whether they should proceed with interaction with certain contacts.
Online Social Networks (OSNs) are a fertile medium through which users can unleash their opinions and share their thoughts, activities and knowledge of various topics and domains. This medium allows legitimate users as well as spammers to publish their content, leveraging the open environment and fewer restrictions associated with OSNs. Hence, it is essential to evaluate users' credibility in various domains and accordingly make judgements about potentially influential users in a particular domain(s). Most of the existing trustworthiness evaluation approaches of users and their posts in OSNs are generic-based approaches. There is a lack of domain-based trustworthiness evaluation mechanisms. In OSNs, discovering users' influence in a specific domain has been motivated by its significance in a broad range of applications such as personalized recommendation systems and expertise retrieval. The aim of this paper is to present a preliminary approach to evaluating domain-based user's trustworthiness in OSNs. We provide a novel distinguishing measurement for users in a set of knowledge domains. Domains are extracted from the user's content using semantic analysis. In order to obtain the level of trustworthiness, a metric incorporating a number of attributes extracted from content analysis and user analysis is consolidated and formulated considering temporal factor. The approach presented in this paper is promising since it provides a fine-grained trustworthiness analysis of users and their domains of interest in the OSNs.
ArXiv, 2021
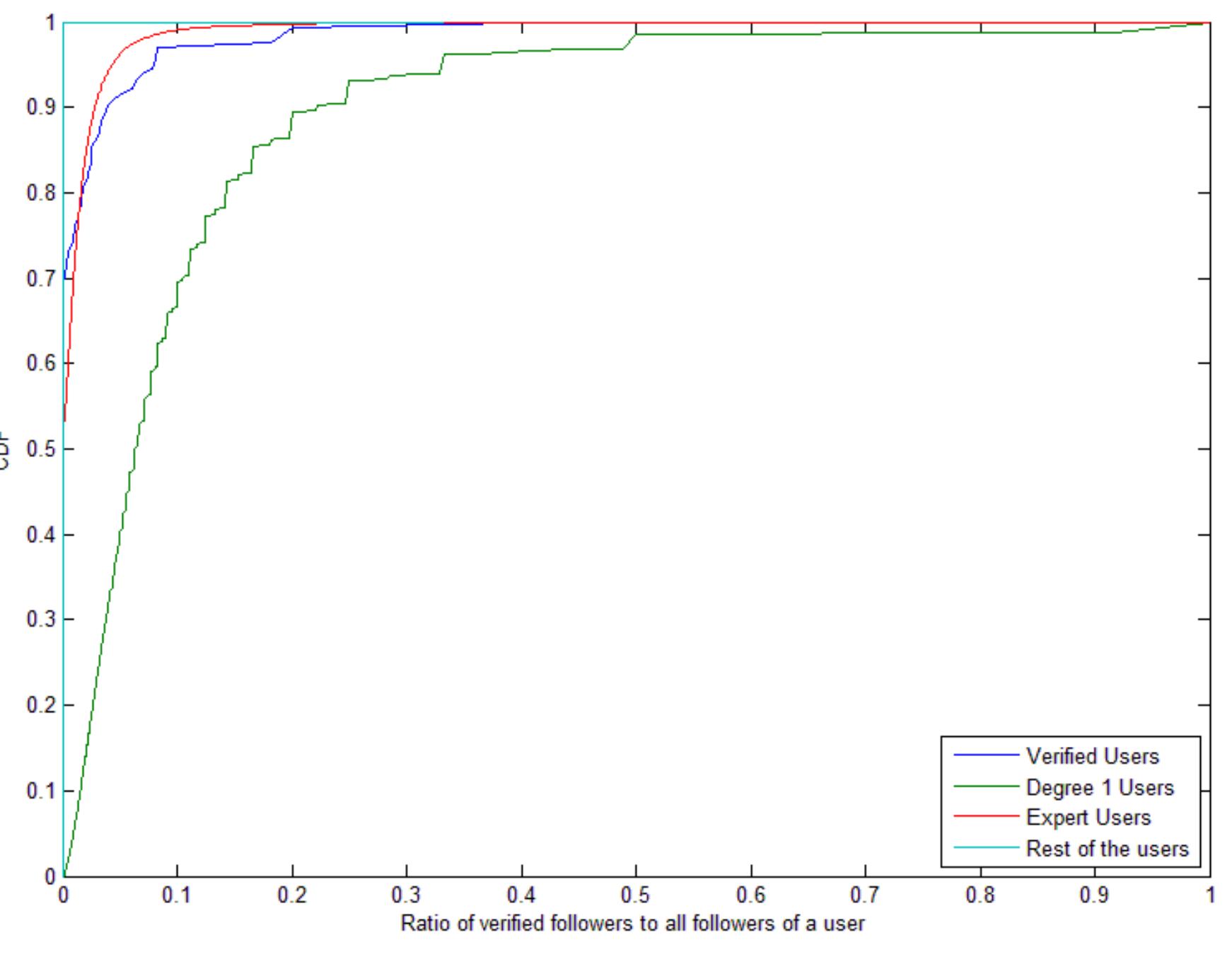
Veracity of data posted on the microblog platforms has in recent years been a subject of intensive study by professionals specializing in various fields of informatics as well as sociology, particularly in the light of increasing importance of online tools for news spreading. On Twitter and similar sites, it’s possible to report on ongoing situations globally with minimal delay, while the cost of such reporting remains negligible. One of the most important features of this social network is that content delivery can be customized to allow users to focus only on news items covering subject matters they find interesting. With this in mind, it becomes necessary to create verification mechanisms that can ascertain whether the claims made on Twitter can be taken seriously and prevent false content from spreading too far. This study demonstrates an innovative System for verification of information that can fulfill the role described above. The System is comprised of four mutually connecte...
Journal of Industrial and Intelligent Information, 2013
We are using combination of data-mining and text-mining techniques to measure opinion, influence, and trust spread in Social Networks within the domain of political elections. In particular we study the case of Twitter and focus on three 2012 presidential elections: the American, the French, and the Egyptian. We propose a new real-time analytic tool for elections. The proposed tool collects live tweet streams on frequent time intervals from followers of presidential candidates and computes a mix of qualitative and quantitative indicators to measure our three parameters (metrics dashboard). English, French and Arabic tweets are analyzed taking into consideration important context background information. We focus more on "Arabic," and present three "Tweet Coloring" algorithms that speculate voters' inclination and impression about the candidates and the influence of the candidates on the voters. On the other hand, three "Edge Coloring" algorithms are used to speculate on opinion, influence, and trust spread (cascading) through Twitter social network graphs. The algorithms compute inferred value ratings through polling neighbors and weighted averaging. A prototype of the proposed tool is implemented on-top of "Nodexl"; an open source template for Microsoft Excel that allows automated connection to a social network server and import (Using Twitter APIs) any data stream into the usual Excel environment. Tweet coloring and Edge coloring algorithms are implemented as Excel Macros with selective setting to either surface, shallow, or deep analysis parameters. Visualization graphs are provided that allow dynamic filtering, vertex grouping, adjusted appearance (zoom into areas of interest), graph metric calculations, etc. Index Terms-text mining; social networks; opinion; influence; trust; analytic tool; and Q-wordnet I.
As the web is being overtaken by the user generated content and interactions, the question has become increasingly important that what and whom to trust. Fortunately, it has become easier to indicate, for the users to who they want to and who they do not want by the help of online social networks and social media. However, the problem is not solved as every use is only likely to know a very small fraction of other users; researchers should have strategies for restraining trust -and distrust -between users who do not know one another. In this paper, different techniques of trust computation is reviewed and analyzed for negative and positive trust.Several techniques used conjunction with a conclusion algorithm which depends on the possible understanding of a trust based on a irregular graph, which happens with the Spring-embedding algorithm.
Services Transactions on Big Data, 2015
In Online Social Networks (OSNs) there is a need for better understanding of social trust in order to improve the analysis process and mining credibility of social media data. Given the open environment and fewer restrictions associated with OSNs, the medium allows legitimate users as well as spammers to publish their content. Hence, it is essential to measure users' credibility in various domains and accordingly define influential users in a particular domain(s). Most of the existing approaches of trustworthiness evaluation of users in OSNs are generic-based approaches. There is a lack of domain-based trustworthiness evaluation mechanisms. In OSNs, discovering users' influence in a specific domain has been motivated by its significance in a broad range of applications such as personalized recommendation systems and expertise retrieval. The aim of this paper is to present an approach to analysing domain-based user's trustworthiness in OSNs. We provide a novel distinguishing measurement for users in a set of knowledge domains. Domains are extracted from the user's content using semantic analysis. In order to obtain the level of trustworthiness, a metric incorporating a number of attributes extracted from content analysis and user analysis is consolidated and formulated by considering temporal factor. We show the accuracy of the proposed algorithm by providing a fine-grained trustworthiness analysis of users and their domains of interest in the OSNs using big data Infrastructure.
Social information systems are a promising new paradigm for large-scale distributed information management, as evidenced by the success of large-scale information sharing communities, social media sites, and web-based social networks. But the increasing reliance on these social systems also places individuals and their computer systems at risk, creating opportunities for malicious participants to exploit the tight social fabric of these networks. With these problems in mind, this manuscript presents the SocialTrust framework for enabling trusted social information management in Internet-scale social information systems. Concretely, we study online social networks, consider a number of vulnerabilities inherent in online social networks, and introduce the SocialTrust framework for supporting tamper-resilient trust establishment. We study three key factors for trust establishment in online social networks -trust group feedback, distinguishing the user's relationship quality from trust, and tracking user behavior -and describe a principled approach for assessing each component. In addition to the SocialTrust framework, which provides a network-wide perspective on the trust of all users, we describe a personalized extension called mySocial-Trust, which provides a user-centric trust perspective that can be optimized for individual users within the network. Finally, we experimentally evaluate the SocialTrust framework using real online social networking data consisting of millions of MySpace profiles and relationships. While other trust aggregation approaches have been developed and implemented by others, we note that it is rare to find such a large-scale experimental evaluation that carefully considers the important factors impacting the trust framework. We find that SocialTrust supports robust trust establishment even in the presence of large-scale collusion by malicious participants.
2013 International Conference on Social Computing, 2013
Increased popularity of microblogs in recent years brings about a need for better mechanisms to extract credible or otherwise useful information from noisy and large data. While there are a great number of studies that introduce methods to find credible data, there is no accepted credibility benchmark. As a result, it is hard to compare different studies and generalize from their findings. In this paper, we argue for a methodology for making such studies more useful to the research community. First, the underlying ground truth values of credibility must be reliable. The specific constructs used to define credibility must be carefully defined. Secondly, the underlying network context must be quantified and documented. To illustrate these two points, we conduct a unique credibility study of two different data sets on the same topic, but with different network characteristics. We also conduct two different user surveys, and construct two additional indicators of credibility based on retweet behavior. Through a detailed statistical study, we first show that survey based methods can be extremely noisy and results may vary greatly from survey to survey. However, by combining such methods with retweet behavior, we can incorporate two signals that are noisy but uncorrelated, resulting in ground truth measures that can be predicted with high accuracy and are stable across different data sets and survey methods. Newsworthiness of tweets can be a useful frame for specific applications, but it is not necessary for achieving reliable credibility ground truth measurements.
References (10)
- Wikipedia article on Twitter. http://en.wikipedia.org/wiki/Twitter
- About Twitter. https://about.twitter.com/company
- H. Kwak, C. Lee, H. Park, and S. Moon. What is Twitter, a social network or a news media? In Proc. Of WWW'10, Raleigh, NC, USA, May 2010.
- Maksym Gabielkov, Ashwin Rao, and Arnaud Legout. Studying Social Networks at Scale: Macroscopic Anatomy of the Twitter Social Graph. To appear in Proc. of ACM SIGMETRICS'14, June 16--20, 2014, Austin, Texas, USA.
- Mashable.com: Eight social media hoaxes you fell for this year. http://mashable.com/2012/11/05/social-media-hoaxes/
- FAQs about verified accounts. https://support.twitter.com/articles/119135-faqs- about-verified-accounts
- Can becoming a twitter 'verified user' help your business? http://www.forbes.com/sites/drewhendricks/2013/09/25/can-becoming-a-twitter- verified-user-help-your-business/
- N. Sharma, S. Ghosh, F. Benevenuto, N. Ganguly, K. P. Gummadi. Inferring Who- is-Who in the Twitter Social Network. 4th ACM SIGCOMM Workshop On Social Networks (WOSN), Helsinki, Finland, August 2012.
- The Least Popular Verified Twitter Accounts (August 2012). http://www.buzzfeed.com/katienotopoulos/the-least-popular-verified-twitter- accounts
- Mashable.com. Facebook Is Most Popular Social Network for All Ages; LinkedIn Is Second [STUDY]. http://mashable.com/2011/11/04/facebook-most-popular-forrester/
 Evgeny Morozov
Evgeny Morozov