Candidate in Diabetic Retinopathy (DR).Purpose is to detect aberrant from color fundus images. Pixels with number of lesions can be illuminated by region Segmentation Using color space selection. In the proposed method simple color... more
Virtualization has gained astonishing popularity in recent decades. It is applied in several application domains, including mainframes, personal computers, data centers, and embedded systems. While the benefits of virtualization are no... more
Catalogue (exhibition in Rome - Sala 1; in Gazoldo - MAM Museum of Modern Art) Works by Ali Assaf, Peter Assmann, Kateryna Lysowenko, Lisl Ponger, Michael Vonbank curated by Paola Artoni, Mary Angela Schroth, Beate Sprenger This... more
Paper is concerned with the study of various edge detection techniques like Prewitt, Robert and Sobel on various images to detect edges and extract its data statistics. Edge detection is a name for set of mathematical methods which aim at... more
Cloud computing provides access to a set of resources such as virtual machines, storage and network as services. In this context, virtualization has been used as a platform for resource-intensive applications, like Hadoop, as it has... more
High efficiency video coding (HEVC) is the newest video codec to increase significantly the coding efficiency of its ancestor H.264/Advance Video Coding. However, the HEVC delivers a highly increased computation complexity. In this paper,... more
Individuals' recognition has been the major concern of many computer science scholars. This paper highlights the development of a biometric fingerprint recognition system using an artificial intelligence method. The methodology used is... more
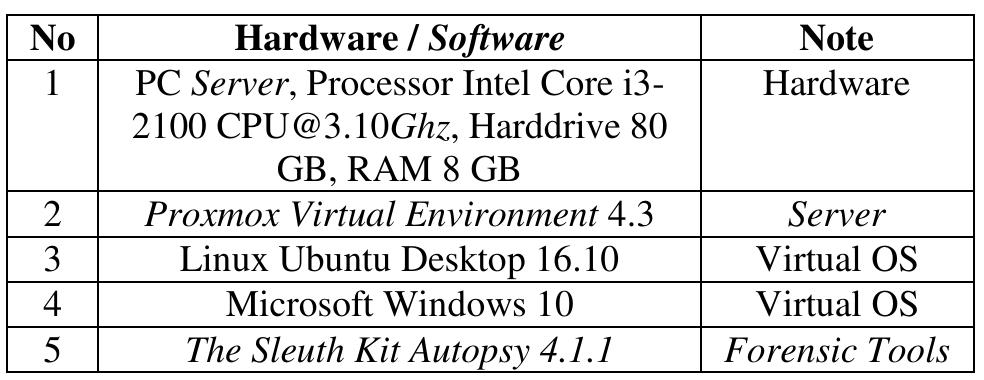
Digital forensics has become a fundamental requirement for law enforcement due to the growing volume of cyber and computer-assisted crime. Whilst existing commercial tools have traditionally focused upon string-based analyses (e.g.,... more
Nowadays personal identification or verification has become one of the most prominent issues in security management. In order to restrict access to secure systems multibiometric refers to authentication techniques that rely on measurable... more
Fingerprints are used as unique identity of people for very long time. The large numbers of fingerprints are collected and stored everyday in a wide range of applications. Since large volume of fingerprint data stored in a database... more
Server virtualization technology has experienced significant development so that more and more industries are adopting this technology. By using server virtualization, the industry can make savings in purchasing new servers and... more
We present a novel approach to liveness verification based on visual speech recognition within a challenge-based framework which has the potential to be used on mobile devices to prevent replay or spoof attacks during Facebased liveness... more
Six Sense Technology, a revolutionary innovation in the field of Human-Computer Interaction (HCI), enables seamless integration of digital information with our physical world, thereby augmenting our sensory perceptions. Developed by MIT... more
Character Recognition (CR) has been extensively studied in the last half century and progressed to a level, sufficient to produce technology driven applications. The preprocessing of characters comprises bounding of characters for... more
The emergence of cloud computing as a ubiquitous platform for elastically scaling services has generated need and opportunity for new types of operating systems. A service that needs to be both elastic and resource efficient needs A)... more
Immeasurable thanks goes to the Almighty God for granting me the grace and direction to complete this thesis. My gratitude goes to my parents Mr. and Mrs. Daniel Ani and my siblings, my family members, friends and my dear Sarah Garba... more
We present a novel approach to liveness verification based on visual speech recognition within a challenge-based framework which has the potential to be used on mobile devices to prevent replay or spoof attacks during Facebased liveness... more
Digital content copyright protection is a key concern in the current environment where intellectual property is constantly threatened. In this paper, a novel solution is proposed to guarantee authenticity and integrity of a text document... more
Young people are fascinated by new information and communication technologies. This is evident in the attraction to social networks and new modes of communication offered by mobile telecommunication networks. Beyond communicating with... more
The advancement in telecommunication network and computer based communication is of great importance in global communications, especially on young adults that constitute the sample of the study. In most mobile telecommunication services,... more
To ensure the accuracy and efficiency of intruder identification, the proposed method is combined with Haar classifier technology for face detection. When someone comes to the door, the Pi camera captures the image and starts the face... more
We expose and explore technical and trust issues that arise in acquiring forensic evidence from infrastructure-as-aservice cloud computing and analyze some strategies for addressing these challenges. First, we create a model to show the... more
We expose and explore technical and trust issues that arise in acquiring forensic evidence from infrastructure-as-aservice cloud computing and analyze some strategies for addressing these challenges. First, we create a model to show the... more
Today, in the era of cutting-edge technology, demand for the reliable security system is increasing and so the biometric based authentication system. Several biometric based systems such as fingerprint and face recognition are used in... more
AbstrakPenelitian ini bertujuan untuk mengetahui hasil karya siswa yaitu dalam menggambar bentuk siswa kelas VIII SMP Negeri 12 Pematangsiantar berdasarkan prinsip-prinsip seni rupa. Objek yang digambar adalah guci. Adapun populasi dalam... more
We propose an optical security technique for image encryption using triple random phase encoding (TRPE). In the encryption process, the original image is first double random phase encrypted. The obtained function is then multiplied by a... more
Nowadays, many pedestrians are injured or killed in traffic accidents. As a result, several artificial vision solutions based on pedestrian detection have been developed to assist drivers and reduce the number of accidents. Most... more
Image enhancement is the process used to enhance the image. There are various techniques of image enhancement which is broadly classified into two categories: Spatial domain and Frequency domain. Spatial domain methods operate directly on... more
We propose a new nonlinear optical architecture based on a focus tunable lens and an iterative phase retrieval algorithm. It constitutes a compact encryption system that uses a single-random phase key to simultaneously encrypt (decrypt)... more
Abstract: The purpose of this study was to create a learning media for color combination recognition that serves to help introduce colors and color combinations to the students of Al-Amin 3 Cemani Kindergarten. The stages of developing... more
This work is devoted to one new approach for decomposition of images represented by matrices of size 2 n 2 n , based on the multiple application of the Singular Value Decomposition (SVD) over image blocks of relatively small size (22),... more
An asymmetric cryptosystem is presented for encrypting multiple images in gyrator transform domains. In the encryption approach, the devil’s spiral Fresnel lens variable pure phase mask is first designed for each image band to be... more
The emergence of cloud computing as a ubiquitous platform for elastically scaling services has generated need and opportunity for new types of operating systems. A service that needs to be both elastic and resource efficient needs A)... more
Embedding a hidden bits stream in a file is named Digital Watermarking. The file could be a text, an image, an audio, or a video. Actually, digital watermarking has many applications like broadcast monitoring, owner identification, proof... more
This research work proposes a lens less secure symmetric image encryption system using a novel chaotic deterministic phase mask (CDPM) in the light of Fresnel transform (FrT) deploying singular value decomposition (SVD). Here, two CDPM's... more
This research work proposes a novel asymmetric scheme by utilizing the hybrid phase truncated fractional Fourier and Gyrator transform with the secure enhancement by adding Kronecker product as a key. In this cryptosystem, the encryption... more
In this paper we present an approach for Human computer Interaction (HCI), where we have tried to control the mouse cursor movement and click events of the mouse using hand gestures. Hand gestures were acquired using a camera based on... more
Nowadays, many pedestrians are injured or killed in traffic accidents. As a result, several artificial vision solutions based on pedestrian detection have been developed to assist drivers and reduce the number of accidents. Most... more
This study builds up two parallel algorithms to improve computing performance for two listing binary and listing permutation algorithms. The problems are extremely interesting and practically applicable in many fields in our daily life.... more
Elimination of combined Gaussian and impulse noises in digital image processing with preservation of image details and suppression of noise are challenging problem. For this purpose, a new filter which is median filters combined with... more
Edge detection is the most frequently and important used operations in image analysis. The edges of the image defined the boundaries and regions of the image. In this paper several edge detection techniques have been applied on Equalized... more
Edge detection belongs to the category of image segmentation techniques which extracts edges/lines within the image. Generally speaking, an edge consists of the boundary pixels which connect two separate regions with different attributes... more
An asymmetric cryptosystem for phase images is proposed which uses amplitude and phase truncation operators in fractional Fourier domain. LU decomposition and Arnold transform are applied to further strengthen the cryptosystem. Analysis... more
Digital content copyright protection is a key concern in the current environment where intellectual property is constantly threatened. In this paper, a novel solution is proposed to guarantee authenticity and integrity of a text document... more
This paper presents two different aspects of cryptanalysis of the optical phase-truncated Fourier transform (PTFT)-based cryptosystem. In the first part, a comparative study is carried out for a specific attack on the PTFT-based scheme in... more
The increasing use of digital video has put into perspective the storage requirements for a large number of video files. Different qualities of videos are available and each of these requires different storage areas. Different variety of... more
The composition of multimedia presentations is a time-and resource-consuming task if not afforded in a well-defined manner. This is particularly true when people having different roles and following different high-level directives,... more
Sixth sense device is a gesture recognition device which uses hand gestures for recognition and performing various operations. Color segmentation is an important task for sixth sense device after color recognition. A RGB color space is an... more
This is a design narrative for a game developed for a Socio-psychology in Design university course. The narrative walks you through course delivery, course content, the challenge, the background research, and the design solution. It is... more
A new encryption scheme using phase masks based on devil's vortex Fresnel lens (DVFL) has been presented in this study. The encryption is performed using fractional Hartley transform (FRHT) in both spatial and frequency domains. Prior to... more