Video Authentication- An Overview
2011, International Journal of Computer Science & Engineering Survey
https://doi.org/10.5121/IJCSES.2011.2406Abstract
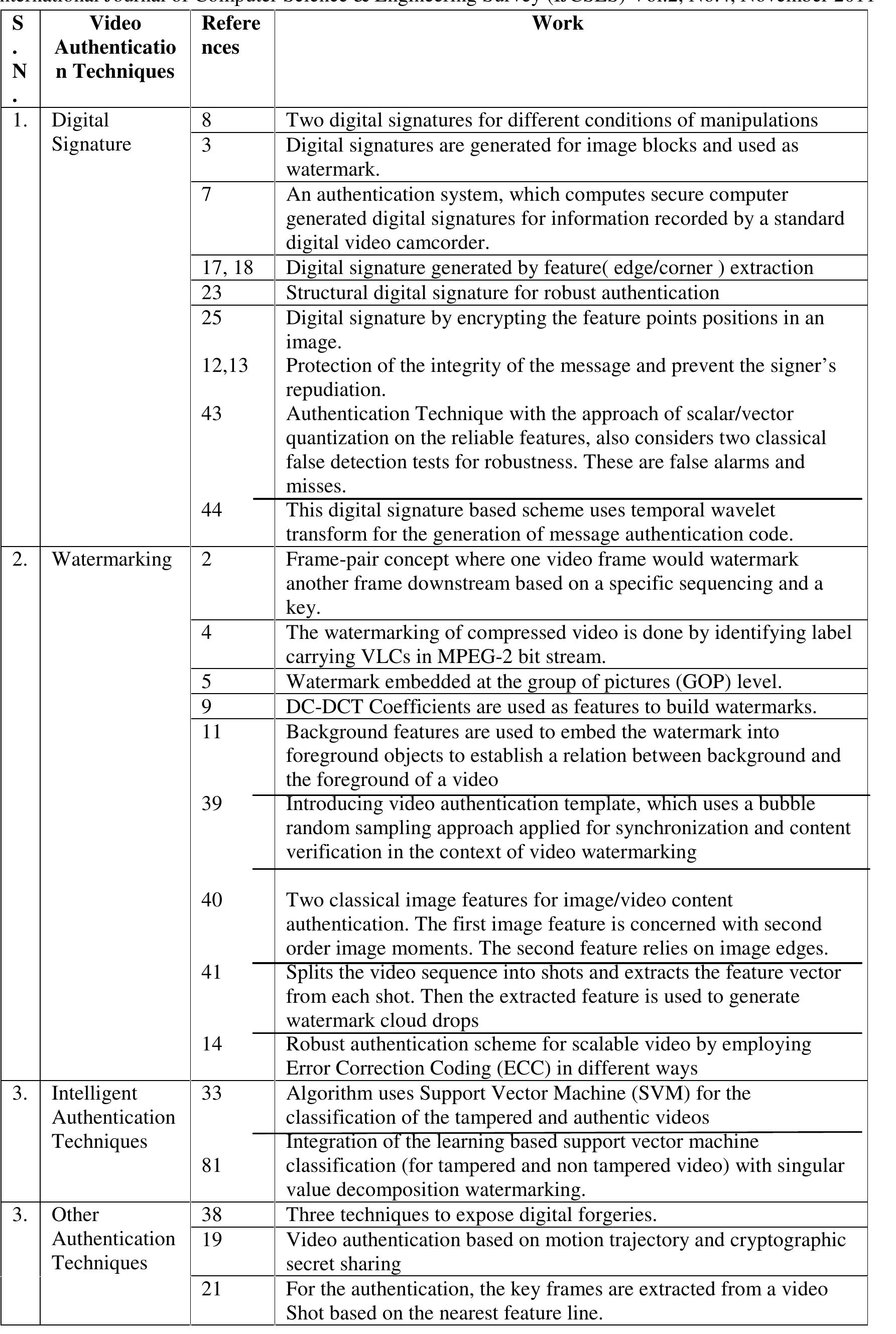
With the innovations and development in sophisticated video editing technology and a wide spread of video information and services in our society, it is becoming increasingly significant to assure the trustworthiness of video information. Therefore in surveillance, medical and various other fields, video contents must be protected against attempt to manipulate them. Such malicious alterations could affect the decisions based on these videos. A lot of techniques are proposed by various researchers in the literature that assure the authenticity of video information in their own way. In this paper we present a brief survey on video authentication techniques with their classification. These authentication techniques are broadly classified into four categories: digital signature based techniques, watermark based techniques, intelligent techniques and other techniques. Furthermore we give the shortcomings of different categories of video authentication techniques in brief.
FAQs
AI
What explains the increase in video manipulation accessibility?
The rise of affordable and sophisticated video editing software has significantly increased access to content manipulation, complicating verification. As of 2023, tools are readily available, allowing even unskilled users to perform tampering.
How do spatio-temporal attacks differ from other tampering methods?
Spatio-temporal attacks manipulate both spatial contents and temporal dependencies between video frames, complicating detection. The classification shows that identifying such attacks requires understanding modifications in both dimensions.
What are the components of an ideal video authentication system?
An ideal video authentication system must support sensitivity to malicious alterations, localization of changes, and robustness against typical processing operations. According to recent studies, it should also mitigate against both false positives and negatives in detection.
When did intelligent techniques for video authentication gain prominence?
Intelligent techniques, such as those employing Support Vector Machines, became prominent around 2015 for their database-driven classification efficiency. These techniques demonstrate high accuracy, for instance, achieving up to 99.92% classification rates in specific studies.
How effective are digital signatures compared to watermarking in video authentication?
Digital signatures provide stronger integrity verification due to their stable characteristics against pixel modifications, outperforming fragile watermarking methods in robustness. However, if the storage location of the signature is compromised, the system becomes vulnerable.
References (44)
- B.G Mobasseri, M.S.Sieffert, R.A.Simard, Content Authentication and tamper detection in digital video, Proc. IEEE International conference on Image Processing, Vancouver, September 10-13, 2000.
- B.G.Mobasseri, A.E.Evans, Content dependent video authentication by self water marking in color space, Proc. Security and watermarking of multimedia contents III, vol. 4314 pp.35-46, January 21-26, 2001.
- M.V. Celik et al, Video authentication with self recovery, Proc. Security and watermarking of multimedia contents IV vol. 4314, pp. 531-541, January 21-24, 2002.
- Daniel Cross, B.G. Mobasseri, Water marking for self authentication of compressed video, Proc. IEEE International Conference on Image Processing, Rochester, NY, September 22-25, 2002
- Peng Yin, Hong heather Yu, Classification of Video Tampering Methods and Countermeasures using Digital Watermarking Proc. SPIE Vol. 4518, p. 239-246, Multimedia Systems and Applications IV
- Zeno j. Geradts, Jurrien Bijhold, Forensic Video investigation with real time digitized uncompressed video image sequences p. 154-164, Investigation and Forensic Science Technologies
- Johns Hopkins APL creates system to detect Digital Video Tampering. http://www.jhu.edu/
- Ching-Yung Lin, Shih-Fu Chang, "Issues and Solutions for authenticating MPEG Video" SPIE electronic Imaging 1999. San Jose.
- Peng, Heather, A semi fragile water marking system for MPEG video authentication, ICASSP 2002, Orlando.
- Pradeep K. Atrey, Wei-Qi Yan, Ee-Chien Chang, Mohan S. Kankanhalli, A hierarchical signature scheme for robust video authentication using secret sharing.
- Dajun He, Oibin Sun, Oi Tian, A semi fragile object based video authentication system IEEE ISCAS 2003, Bangkok.
- R. Gennaro and P. Rohatgi, How to sign digital stream, Crypto' 97, pp. 180-197, 1997.
- J. M. Park, E. K. P. Chong and H. J. Siegel, Efficient multicast packet authentication using signature amortization, IEEE symposium on security and privacy, pp. 227-240, 2002.
- Qibin Sun, Dajun He, Zhishon Zhang and Qi Tian, A secure and robust approach to scalable video authentication ICME2003.
- Tsong-Yi Chen, Thou-Ho Chen, Yin-Ting Lin, Yin-Chan Chang, Da-Jinn Wang, H.264 Video authentication based on semi fragile watermarking, DOI 10.1109/IIH-MSP, 2008 IEEE.
- Qibin Sun, Shih-Fu Chang and K. Mean, A new semi fragile image authentication framework combining ECC and PKI infrastructure, ISCAS 2002, Phoenix, May 2002.
- Titman, J.; Steinmetz, A; Steinmetz, R., Content based digital signature for motion pictures authentication and content fragile watermarking, Multimedia computing and systems, 1999. IEEE International Conference on, Volume: 2, 1999, Page(s): 209-213 vol. 2.
- Queue, M. P., Toward robust, content based techniques for image authentication, Multimedia signal processing, 1998 IEEE Second workshop on, 1998 page(s): 297-302.
- Wei-Qi Yan an Mohan S Kankanhalli, Motion Trajectory Based Video Authentication ISCAS (3) 2003: 810-813
- Latechi L. Wildt D. and Hu J., Extraction of key frames from videos by optimal color composition matching and polygon simplification. Proceedings of MMSP' 2000, Cannes, France, October 2001
- Zhao L., Qi W., Li S., Yang S. and Zhang H., Key frame extraction and shot retrieval using Nearest Feature Line (NFL)., Proceedings of ACM Multimedia 2000.
- Quisquater J., Authentication of sequences with the SL2 Hash function application to video sequences, Journal of computer security, 5(3), pp: 213-223, 1997.
- Chun-Shien Lu and Hong Yuan Mark Liao, Structural digital signature for image authentication: An Incidental Distortion Resistant Scheme. IEEE Trans. Multimedia, vol. 5, no. 2, pp. 161-173, Jun. 2003.
- Martinian, E.; Wornell, G. W.; and Chen, B., Authentication with Distortion Criteria, Submitted to IEEE Trans. Information Theory.
- S. Bhattacharjee and M. Kutter, Compression tolerant image authentication, in IEEE International Conference on Image Processing, 1998, pp. 435-439.
- W. Diffie and M. E. Hellman, New Directions in cryptography, IEEE Trans. On Information Theory, Vol. 22, No. 6, pp.644-654, Nov 1976.
- P. Wohlmacher, Requirements and Mechanism of IT-Security Including Aspects of Multimedia Security, Multimedia and Security Workshop at ACM Multimedia 98, Bristol, U. K., Sep. 1998.
- Neil F. Johnson, An Introduction to watermark Recovery from Images, Center for Secure Information System, George Mason University, Fair Fax, VA 220304444
- S. Craver, N. Memon, B. Yeo and N. M. Yeung, Resolving Rightful Ownerships with Invisible watermarking Techniques: Limitations, Attacks and Implications, IEEE Journal on Selected Areas in Communications, Vol. 16, No. 4, pp. 573-586(1998).
- The Oxford English Dictionary, 2
- R. Singh, M. Vatsa, S.K. Singh, and S. Upadhyay, Integrating SVM Classification with SVD Watermarking for Intelligent Video Authentication, In Telecommunication Systems Journal -Special Issue on Computational Intelligence in Multimedia Computing, Springer, 2008 .
- C. I. Podil chuk, N. S. Jayant, and N. Farrardin, Three dimensional sub band coding of video IEEE Trans. Image processing vol. 4 no. 2, 1995, pp.125-139
- Vapnik VN (1995) The nature of statistical learning theory. Springer Verlag.
- Singh R., Vatsa M., Noore A (2006) Intelligent biometric information fusion using support vector machine. In soft computing in Image processing: Recent advances, Springer Verlag 327-350 .
- Kovesi PD (1999) Image features from phase congruency. Videre: Journal of Computer vision research, MIT Press 1(3).
- Kundur, D., Implications for high capacity data hiding in the presence of lossy compression, Information Technology: Coding and Computing, 2000, Proceedings. International Conference on, 27-29 March 2000, Page(s): 16 -21
- Watson, A.B., Visually optimal DCT quantization matrices for individual images, Data Compression Conference, 1993. DCC '93, 30 March-2 April 1993, Page(s): 178 -187.
- Bloom I., Cox I. and Kalker T. Copy Protection for DVD Video. Proceedings of lEEE, July, 1999, 87, 7
- P.K. Atrey, W. Yan, and M.S. Kankanhalli, A scalable signature scheme for video authentication, presented at Multimedia Tools Appl., 2007, pp.107-135.
- S. Chen and H. Leung, Chaotic watermarking for video authentication in surveillance applications, IEEE Trans. Circuits Systems Video Technology, vol. 18, no. 5, pp. 704-709, May 2008 .
- Razib Iqbal, Shervin Shirmohammadi and Jiying Zhao, Compressed Domain Authentication of Live Video, IEEE International Conference on Signal processing and communications (ICSPC 2007) 24-27 November 2007, Dubai, United Arab Emirates.
- Aaron T. Sharp, James Devaney, Austin E. Steiner, Dongming Peng, Digital Video Authentication with motion vector watermarking, 978-1-4244-7907-8/10, 2010 IEEE.
- Bandyopadhyay, P.; Das, S.; Paul, S.; Chaudhuri, A.; Banerjee, M., A Dynamic Watermarking Scheme for Color Image Authentication, Advances in Recent Technologies in Communication and Computing, 2009. ARTCom '09. International Conference on, pp.314-318, 27-28 Oct. 2009.
- Das, S.; Bandyopadhyay, P.; Paul, S.; Ray, A.S.; Banerjee, M.; "A New Introduction towards Invisible Image Watermarking on Color Image," Advance Computing Conference, 2009. IACC 2009. IEEE International, pp.1224-1229, 6-7 March 2009
 Saurabh Upadhyay
Saurabh Upadhyay